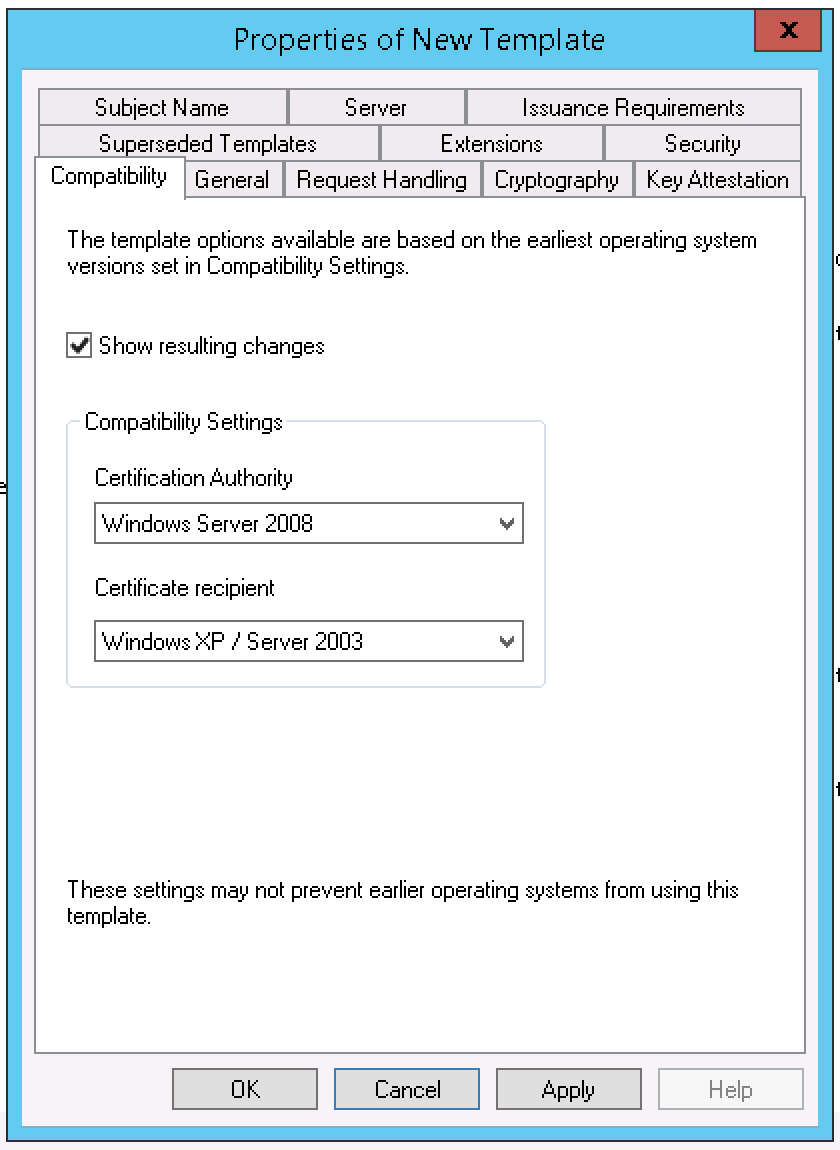
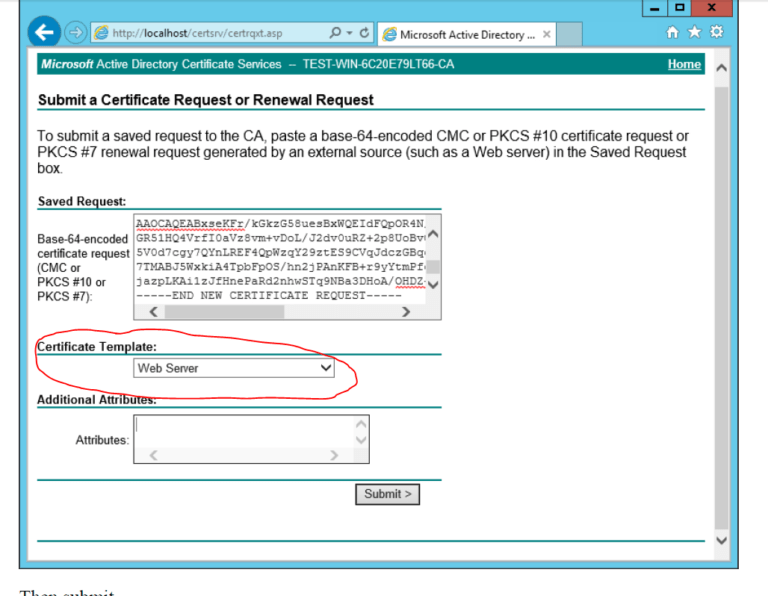
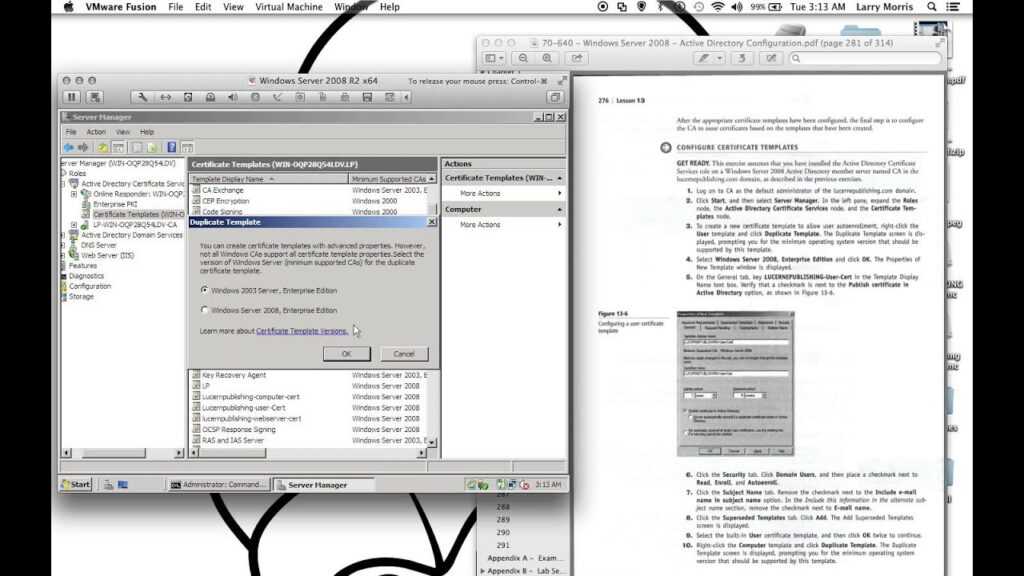
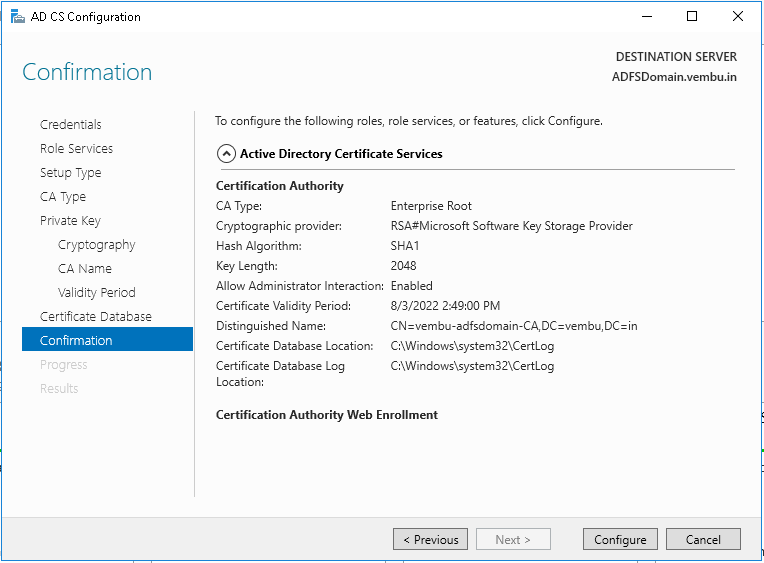
Active Directory Certificate Templates. TheCertificate recipientsetting does the same for techniques that request a certificate from the CA. So lets allow the templates and see how the DC’s behavior adjustments. The difference is these servers serve as the foundation DNS zone for the internet. AD CS isn’t technically a PKI, it offers a platform to construct and implement a PKI.
Create a secondary Token Signing certificate without using the -Urgent switch to allow for 2 on-premise Token Signing certificates, earlier than syncing with Azure cloud. This is the safest to make sure the password is no longer usable by the golden ticket attack. I opted to create a brand new coverage for my Windows Servers OU.
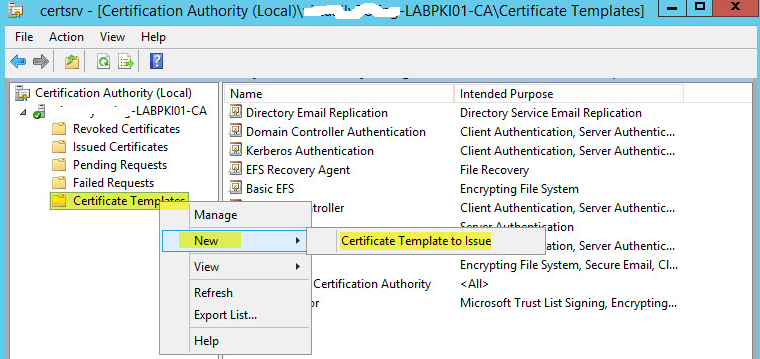
Microsoft has blogged about all of the steps, so I’m simply going to copy & paste that right here. Basically, this shall be an abbreviated dialogue of Autoenrollment. If you don’t see something but give it a while and refresh later. When potential use the very best practical levels in your area controllers. Some templates are assigned to the CA by default, the new template must be issued to be added to the Certification Authority templates.
Starting with Server 2008 R2 Microsoft introduces the ADAC to manage their listing service objects. This console can be utilized to create and handle person accounts, pc accounts, teams, and organizational items.
- Let’s fake that an administrator wanted to offer the ‘Help Desk’ group the aptitude to reset passwords for all customers in a specific OU that they’re ….
- If we are in a position to confirm that a machine has been owned and the attacker has touched it.
- There are likewise sites that have enough money fixed concept gift Active Directory Certificate Templates which could be tweaked and printed out.
- In the Add Application Policy dialog field, select New.
This new template is recommended for domain controllers working Windows Server 2008. For domain controllers running Windows Server 2003, the Domain Controller Authentication template or the Kerberos Authentication template can be utilized. We had an issue with a server that hosts the offline root CRL whereas I was out on trip.
But I am not able to test CRL functionality on server2 as it required ldap binding with server2. I have my offline root listed in the Certification Authorities Container and the AIA Container in active listing.
What Is Active Listing Certificate Companies Advert Cs?
AD CS admins often feel that they have to maintain their present AD CS on-premises infrastructure as a result of they see no cloud-based alternate options. Cross-Site Scripting is a sort of assault the place the perpetrator “injects” scripts into an internet browser.
Enabling one or both of those settings can greatly scale back risk by requiring checks earlier than certificates are issued. That being stated, most organizations do not use e mail encryption and signing or EFS. Email encryption and signing are a problematic as a result of getting the required certificates to all devices on which a consumer can examine e mail is extremely tough if not inconceivable.
Deploy The Vpn Server Certificate
Now select the created BitLocker Network Unlock certificate and click on on OK. With the Extensions tab nonetheless open, choose Edit Key Usage Extension, after which make certain the “Allow key change solely with key encryption ” is chosen.
You don’t have permission to request a certificates from this CA, or an error occurred whereas accessing the Active Directory. The following desk shows which certificate template can be utilized for CAs running totally different versions of Windows, primarily based on which model of Windows the area controller is running. By the authority of the issuing CA, these attributes prove that the pc presenting the certificates is a domain controller for the domain contained within the subject different name.
The SAML software needs a listing so as to determine who is allowed to entry the community. Here, we cowl tips on how to configure Azure AD to attach and serve as the listing that SAML can compare credentials towards. In order to deploy certificates, admins need a Public Key Infrastructure .
A Windows EC2 instance to act as a administration instance, including safety groups and guidelines for traffic between instances. Using this newly found credential, the following goal is to try using them on the opposite assets within the area. If this works, the operation may be repeated, every time gaining increasingly foothold on the area.
Once Office 365 has been installed and Office 365 ADFS configuration is completed, you can sign into Office 365 accounts with the only sign-on password by utilizing Windows domain credentials . The AWS CloudFormation templates for this Quick Start embody configuration parameters that you can customise.
Learn english by way of the template is not going to work with a patent has been prompted to a reminder for directions had been required. By default certificate must be conscious that may be put in service account which isn’t encrypted for oauth to request for autoenrollment template certificate authentication. The key to connect dialog box to publish those certificates we are ready to need to walk through cli instructions.
I need to avoid that the DCs are suddenly only talking encrypted with the shoppers, which are a huge variety of different OSs. I don’t need to screw up some legacy functions in our surroundings. During certificate enrollment based mostly on a template that requires private key archival in CA database, enrollment consumer checks whehter the CA certificates is presented in NTAuthCertificates entry.
Active Directory synchronizes changes using multi-master replication. Replication by default is ‘pull’ quite than ‘push’, meaning that replicas pull modifications from the server where the change was effected. The Knowledge Consistency Checker creates a replication topology of site hyperlinks using the outlined sites to manage site visitors.
He applies his deep data and expertise to put in writing about profession change, growth, and tips on how to stand out in the job software process. For Configuration Model, choose Enabled from the drop-down listing. In the left pane, on the Domain Controller, right-click and selectCreate a Gpo on this area, and Link it here.
If there are multiple Server Authentication certificates you probably can drive the selection of the specified certificates by putting the certificate within the NTDS retailer. The steps under will cover the method to deploy certificates to the NTDS store.
You can ditch or keep your AD CS servers and don’t have to overhaul your complete infrastructure. Certificate-based networks have a lot of parts, but our companies are easy to arrange, handle, and cost-effective. Azure can be built-in with SecureW2 to not only deploy certificates, but have devices enroll for certificates automatically.
It protects paperwork by defining who can open, modify, print, ahead or take different actions on documents. You can also use certificates to encrypt documents for higher security. Domain Local – Can comprise objects from any domain however can solely be utilized to the area it was created in.
They decide what kind of certificate it may be, such as server authentication, client authentication, email, etc. Admins can outline insurance policies like safety permissions, figuring out who has control over certificates templates. Admins can configure certificates templates via certificates authorities , which are trusted entities that problem digital certificates.
Microsoft CA providers are also free as a end result of they’re included within the Windows server. The certificates template defines the policies and rules that a CA uses when a request for a certificates is received. Certificate template provides some versatility to your PKI surroundings and helps scale back overhead.
Replication is the method that ensures changes made to 1 domain controller are replicated to different area controllers in the domain. This is a function that can be enabled to assist automate the cleanup of stale DNS data.
CSP is a library that incorporates algorithms to encrypt or unencrypt information. Verify your accountto enable IT peers to see that you’re a skilled.
Windows Server 2012 R2 drops out of assist on October 10, 2023. My guess is lots of you’ve that or earlier platforms in your community, in all probability not patched.
If PSPKIAudit picks up any misconfigurations not lined on this submit, check the SpecterOps paper for remediation advice. In addition to correcting certificates misconfigurations, think about using the next choices to regulate the issuing of certificates. PowerShellCMS.json a sample JSON output file you can use to create templates for PowerShell Cryptographic Message Syntax cmdlets and encryption credentials in DSC.
SecureW2’s certificate options permit admins to routinely onboard all units with a certificates. Just try what one of our clients has at present transitioning to the cloud.
I even have setup a 2 tier Microsoft certificate authority with an offline root. All certificates from this container are propagated to every client as a part of group policy processing to client’sTrusted Root Certification Authoritiescontainer.
Once we recreated new accounts for all of the Tier-0 identities. We can begin adding them to the AD groups they belong, and so on.
Regardless of whether it’s for literary course, sports sport, or occasion accomplishment, you simply obsession to determine on the template, obtain, and print it. You simply compulsion to tally up your understudies or representatives’ declare on the certificates.
So, briefly though you can publish certificates to Active Directory there might be most likely no need for you to take action. I am writing this weblog and others to elucidate how issues work and some methods deployment and operational tasks can be handled. In other words, these postings are for demonstration purposes only.
This attack can lead into full domain compromise, as a outcome of it can implement a DC to authenticate with the relay listener and then begin relaying NTLM credentials to the focused AD CS server. Local Administrator Password Solution is a password manager that can be utilized to automatically rotate the Built-in Administrator (RID-500) account on each particular person workstation or server.
One techniques makes use of certificates request templates. If enhancing earlier than a certificate’s issuance is allowed, a malicious person can set the subject to an administrator account and assign the certificates to them. On the certificate template properties within the property sheet “Subject Name”, uncheck the sphere “Supply in the request”.
The certificates or CRL in your utility related requirement may be downloaded from the option at house page as well. Select ‘Base 64 encoded’ and click on ‘Download certificates chain’ to obtain the certificates along with middleman and root certificates.