The world of cybersecurity is constantly evolving, with new threats emerging daily. Organizations of all sizes are facing increasing risks, and effective threat assessment is crucial for proactive defense. A robust threat assessment report provides a structured framework for identifying, analyzing, and prioritizing potential threats, ultimately safeguarding assets and ensuring business continuity. This article will delve into the key components of a comprehensive Threat Assessment Report Template, offering guidance on how to create a valuable tool for your organization. Threat Assessment Report Template is more than just a document; it’s a strategic asset, enabling informed decision-making and effective mitigation strategies. Understanding the principles behind this template is vital for anyone responsible for security risk management.
The initial stages of a successful threat assessment often involve gathering intelligence. This initial phase is critical for establishing a baseline understanding of the threat landscape. It’s about understanding the current environment – what’s happening, what’s likely to happen, and what’s already being targeted. This preliminary assessment informs the subsequent stages of the process, allowing for a more targeted and effective analysis. Without a solid foundation, the entire assessment becomes a reactive exercise, struggling to identify and address emerging threats. A well-executed initial assessment dramatically reduces the time and resources required to respond to potential incidents.
The core of a Threat Assessment Report Template revolves around several key elements. Firstly, a thorough understanding of the organization’s assets is paramount. This includes identifying critical systems, data, and infrastructure. We need to know what we’re protecting – not just where. Secondly, we must assess the organization’s vulnerabilities. This involves identifying weaknesses in systems, processes, and human behavior that could be exploited by attackers. This is where the Threat Assessment Report Template truly shines, providing a structured way to systematically examine these vulnerabilities. A lack of vulnerability assessment can leave an organization significantly exposed.
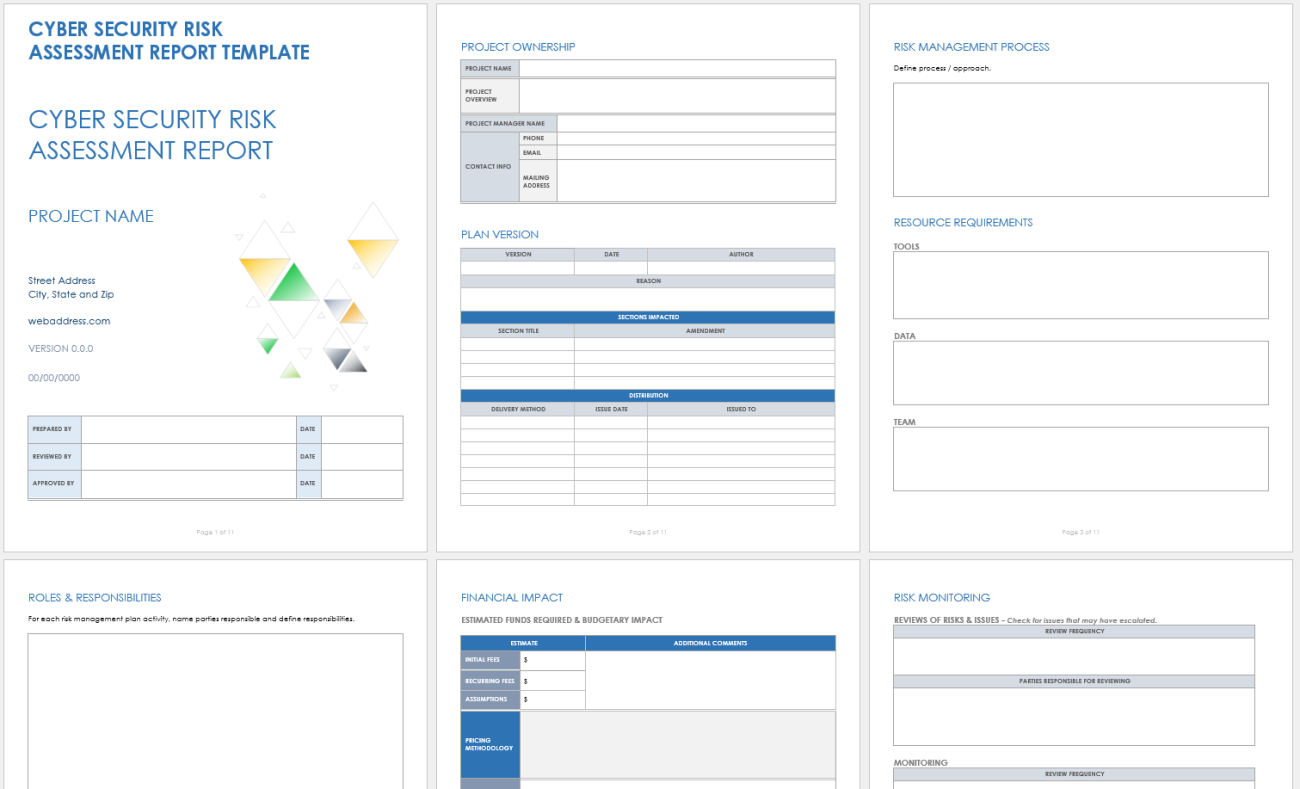
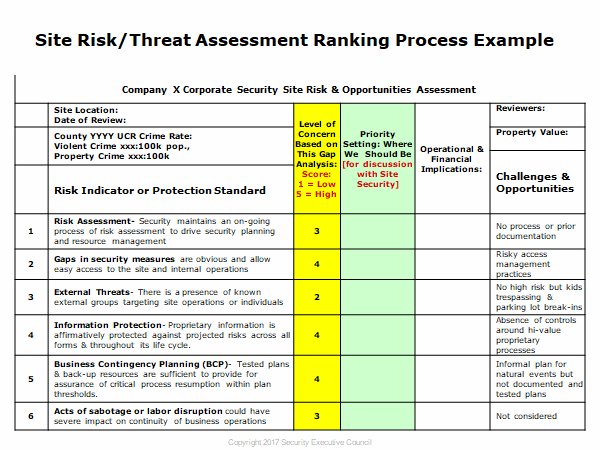
The template typically includes sections dedicated to: Asset Inventory, Vulnerability Assessment, Threat Intelligence, Risk Analysis, and Mitigation Strategies. Let’s examine each of these in detail. The Asset Inventory section is the foundation of the report, detailing everything that constitutes the organization’s value. This goes beyond simple hardware and software; it encompasses data, intellectual property, customer information, and even employee data. Proper documentation of assets is essential for prioritizing remediation efforts. A complete and accurate inventory allows for a clear understanding of what needs protection. Consider using a standardized asset classification system to ensure consistency and facilitate analysis.
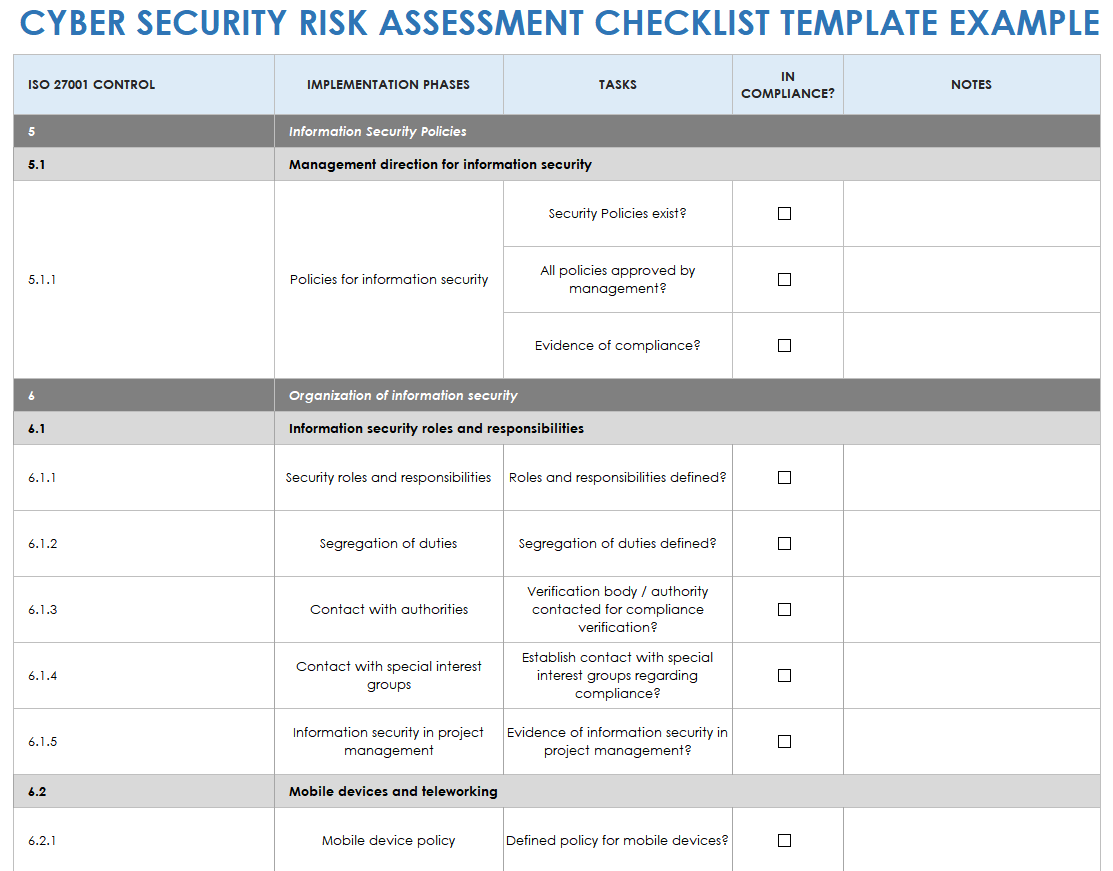
The Vulnerability Assessment component is where the organization actively seeks to identify weaknesses. This can involve penetration testing, vulnerability scanning, and security audits. The Threat Assessment Report Template facilitates this process by providing a framework for systematically testing systems and identifying potential weaknesses. It’s important to remember that vulnerability assessment is not just about finding flaws; it’s about understanding how those flaws could be exploited. The results of this assessment should be clearly documented and prioritized based on risk. Regular vulnerability scanning is a crucial part of maintaining a strong security posture.
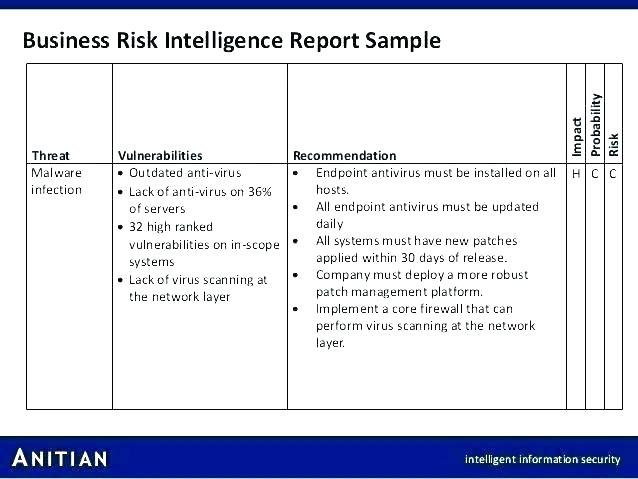
The Threat Intelligence section is where the organization gathers information about potential threats. This includes analyzing threat reports, security blogs, industry news, and other sources to understand emerging trends and attacker tactics. Threat Assessment Report Template allows for the integration of this intelligence, providing context and enabling informed risk assessments. Understanding why attackers are targeting your organization is just as important as knowing what they’re targeting. A proactive threat intelligence approach can significantly enhance your ability to defend against attacks.
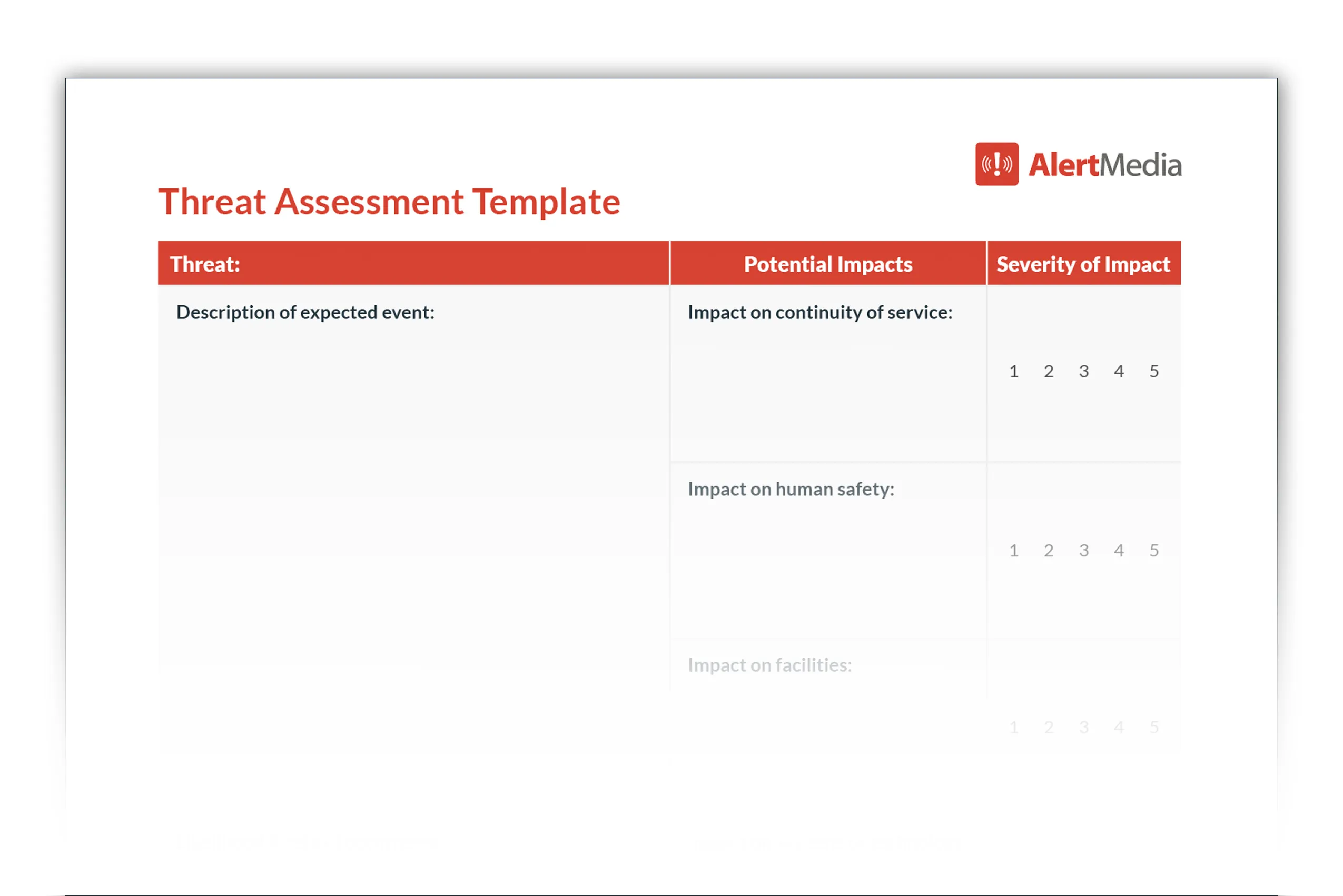
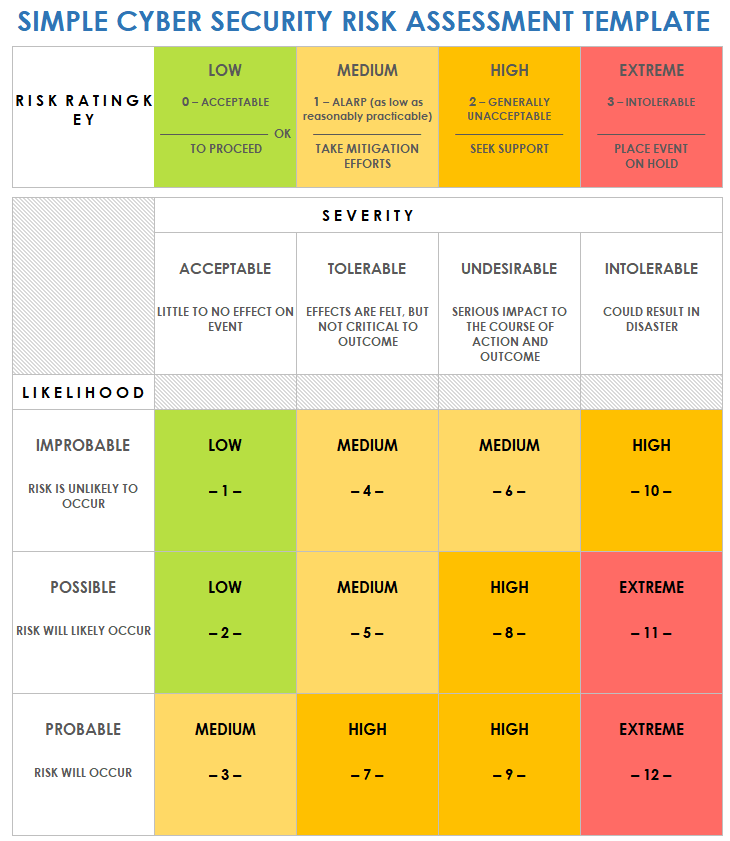
The Risk Analysis section is arguably the most critical component of the template. It involves assessing the likelihood and impact of potential threats. This is typically done using a risk matrix, which helps to prioritize risks based on their potential severity. The Threat Assessment Report Template provides a structured way to calculate risk scores, allowing for a clear understanding of which risks require the most attention. Factors to consider include the potential impact on the organization’s reputation, financial losses, and legal liabilities. A thorough risk analysis is essential for allocating resources effectively.
Finally, the Mitigation Strategies section outlines the actions the organization will take to reduce the identified risks. This could include implementing security controls, improving security awareness training, and developing incident response plans. The Threat Assessment Report Template allows for the detailed documentation of these strategies, ensuring that they are aligned with the organization’s overall security goals. It’s not enough to simply identify risks; you must also develop and implement effective mitigation strategies. A well-defined mitigation plan is a critical component of a successful security program.
The creation of a truly effective Threat Assessment Report Template requires careful planning and execution. It’s not a one-time project; it’s an ongoing process. Regularly reviewing and updating the template is essential to ensure that it remains relevant and effective. Consider incorporating feedback from stakeholders, such as IT staff, security personnel, and business leaders. The template should be adaptable to the specific needs of each organization. Furthermore, utilizing a standardized format and incorporating key metrics will improve the consistency and usability of the report.
In conclusion, a well-crafted Threat Assessment Report Template is an indispensable tool for organizations seeking to proactively manage cybersecurity risks. By systematically identifying, analyzing, and prioritizing threats, this template enables informed decision-making, effective mitigation strategies, and ultimately, a stronger defense against cyberattacks. Investing in a robust threat assessment framework is a critical investment in the long-term security and resilience of your organization. The benefits of a comprehensive approach far outweigh the initial investment. Ultimately, a proactive approach to threat assessment is a key differentiator in today’s increasingly complex threat landscape.
Conclusion
The threat landscape is dynamic and ever-changing, demanding continuous vigilance and adaptation. A robust Threat Assessment Report Template serves as the cornerstone of this vigilance, providing a structured and comprehensive framework for understanding and mitigating potential risks. From identifying critical assets to prioritizing vulnerabilities and evaluating mitigation strategies, this template empowers organizations to proactively defend against evolving threats. By consistently utilizing this tool, organizations can significantly reduce their exposure to cyberattacks, protect their valuable data, and maintain business continuity. The ongoing refinement and adaptation of the Threat Assessment Report Template are crucial for staying ahead of the curve and ensuring a proactive security posture. Ultimately, a proactive approach, informed by a well-executed threat assessment, is the most effective defense against the ever-present threat of cybercrime.